As a researcher that has been working in different institutions already, one of the most common issues I have faced when moving from one place to another is losing access to the network (and “private” resources) of my previous university and/or team.
To access that kind of remote private resources, you’d normally use a VPN connection. But VPN credentials are normally controlled by a central IT service that won’t be allowed to give permissions to somebody that is no longer part of the institution. In such a case, one very easy workaround is just to use an SSH connection to create a tunnel that will redirect your browser’s navigation info through it.
Although there are already quite a few tutorials on the net on how to do this, I’ve been asked too many times on how to do it that I prefer to keep my own tutorial for this. Because of that, next, I will show you how to setup your (Windows) computer so that you can leave the tunnel preconfigured in such a way that can be opened in a few clicks when needed. Sorry for the screenshot with UIs in Spanish! 😅
Prerequisites
To follow this tutorial you’d need:
- A user account in a server where you are allowed to log in via SSH (your SSH server must be configured to allow tunneling). At least for the first login, password authentication must be enabled.
- The PuTTY Windows SSH client.
- A browser supporting different profiles (such as Firefox or Chrome).
Step 0: Create a SSH key
Storing user passwords is considered unsafe. As a consequence, to be able to open a SSH session without manually providing a password each time requires the use of a SSH key.
In PuTTY, these keys can be generated using the PuTTYgen program. You only have to open PUTTYgen, and click on Generate:
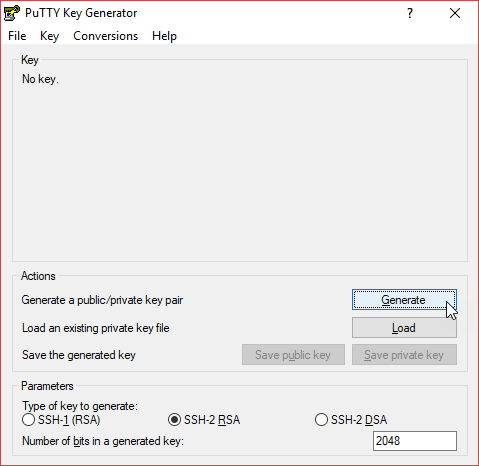
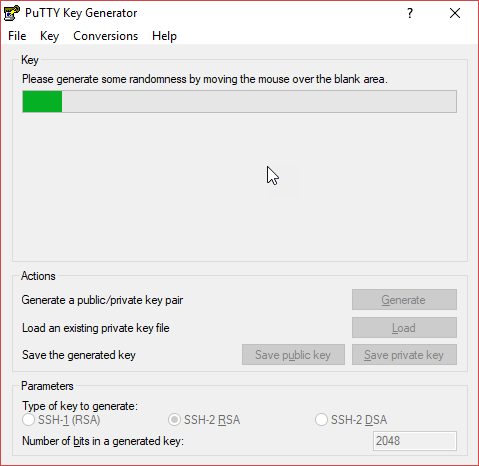
Then, you’d be asked to move your mouse to generate some randomness. The key won’t be generated until the progress bar finishes.
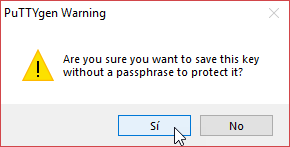
Once the progress finishes, you’ll get the key. If you don’t want to enter a password every time you use the key, you can just leave the password empty. Then, you can save the key on disk by clicking Save private key.
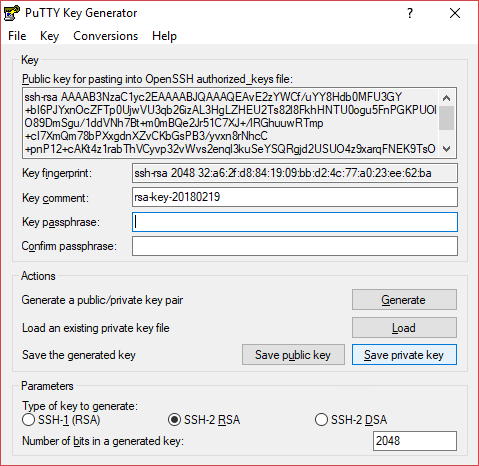
IMPORTANT: Be sure to keep your keys in a safe place since this file is the only thing needed to log in your SSH server!
Private keys are saved with the extension PPK. This file will be later used in PuTTY.
Next, you can save the public key by pressing Save public key:
Public keys do not have a default extension, but you can use PUB.
Finally, you may also want to explicitly save the public key in the form expected by an authorized_keys file (more on this below). Just copy the text in the read-only field to the clicboard, and save it to a file using your preferred editor.
authorized_keys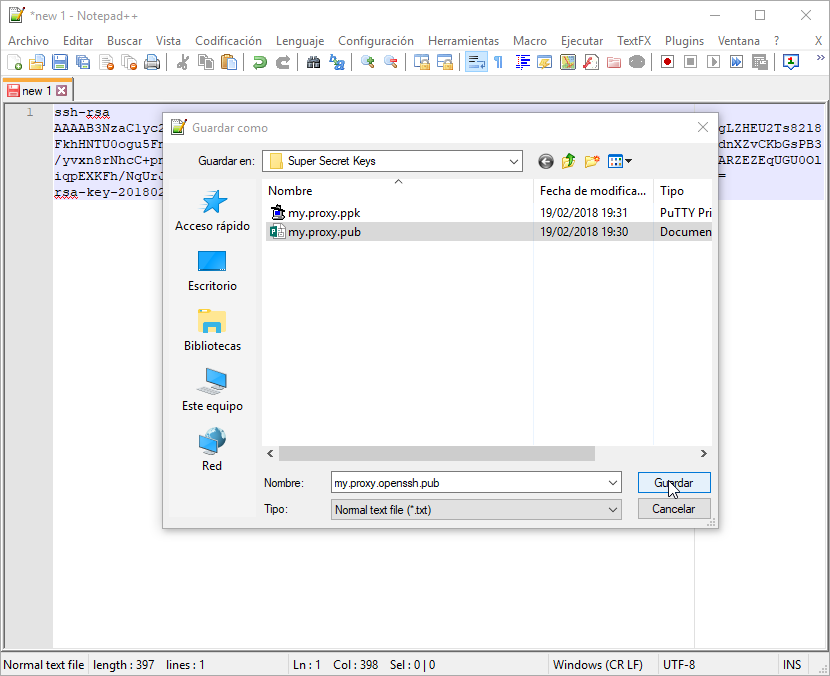
Step 1: Configure the SSH connection in PuTTY
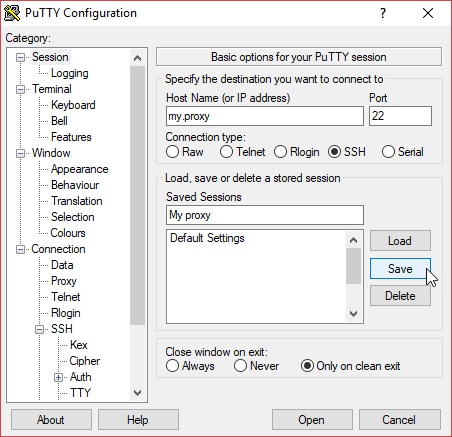
Now that we already have the key, we can set up the SSH connection. The first data that must be specified is the Host Name (or IP address) and the Port of your SSH server.
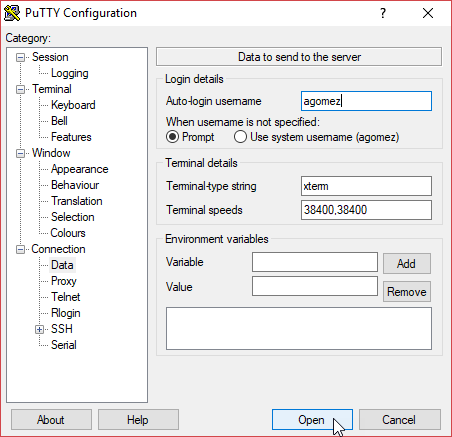
Next, in the Connection > Data Category, you can set your username in the Auto-login username field.
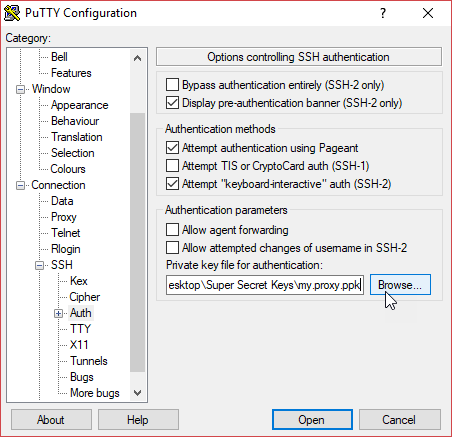
In the Connection > SSH > Auth Category you must point to the SSH private key (the PPK file) you just created in Step 0. This key won’t be valid for the first login (we will install it on the server later, in Step 2), but it will allow us to login without a password from that moment on.
In the Connection > SSH > Tunnels Category, we setup the information for the proxy. A proxy is setup by:
- Specifying the Source port number (e.g., 8080). It must be a free port on your local machine.
- Selecting Dynamic and Auto.
- Pressing Add, and the line D8080 will appear in the big list in the middle of the dialog.
Other port redirections can be specified here. but this is out of the scope of this tutorial 😊.
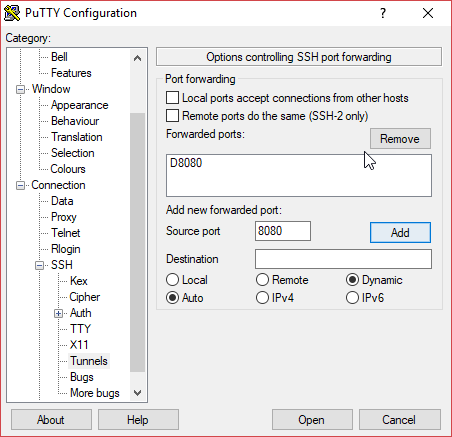
NOTE: It is even possible to use a SSH tunnel to run remote graphical application locally using a local X Server. This is done by enabling X11 forwarding (this is not needed for the web proxy we’re configuring here!). Maybe in the future I write another short tutorial on this 😁.
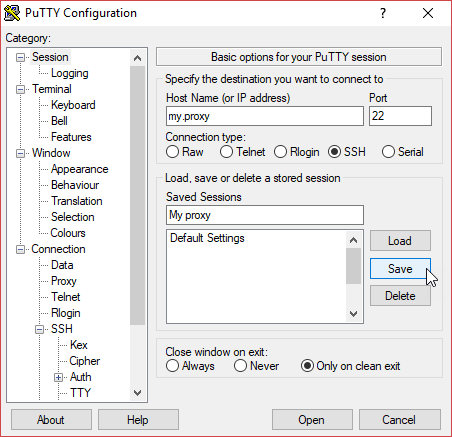
Once all the previous configurations have been set, you can go back to the Session Category, and you can save this session configuration to be reused in the future. You only need to put a name to the session in the Saved Sessions field, and after that, click on Save. To connect to your SSH server in the future, and automatically log in, you’ll only have to double click on the My proxy line of the Saved Sessions list.
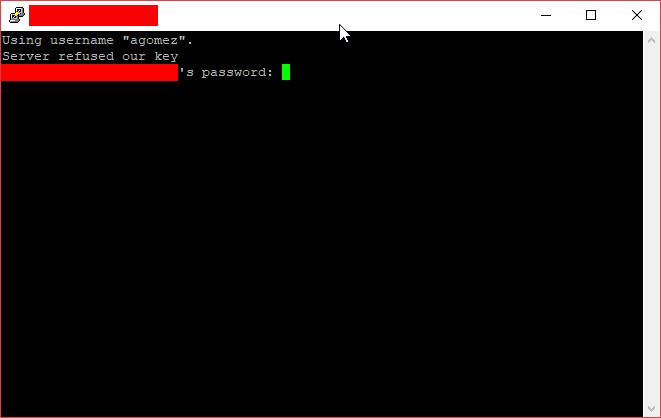
Step 2: Install the SSH key on your user profile in the remote server.
With eveything configured, you can just click on Open (or, as aforementioned, double click in the Saved Session), and a terminal in your remote server will open. Since it is the first time you’re connecting, you’ll be asked for your user password.
Next, you only need to create (or open if it already exists), the .ssh/authorized_keys file in your home directory, and set the proper file permissions (if not, the SSH server will refuse to accept your authorized key). You can do this by running the following commands:
mkdir -p ~/.ssh touch ~/.ssh/authorized_keys chmod 700 ~/.ssh chmod 600 ~/.ssh/authorized_keys
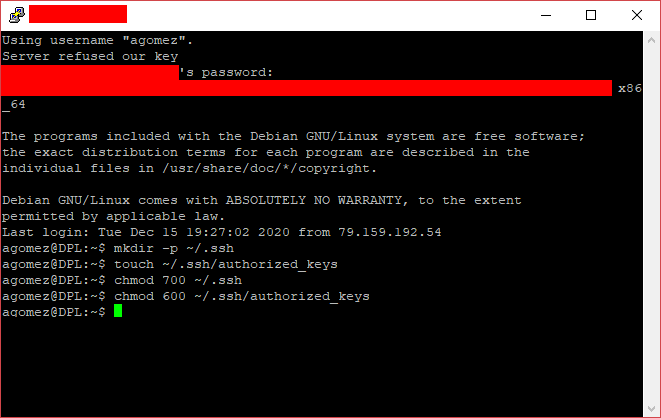
Once all files and permissions have been configured, you can just open the .ssh/authorized_keys file (e.g, using the nano editor), and you can add a line with the public key as expected by OpenSSH we saved at the end of Step 0.
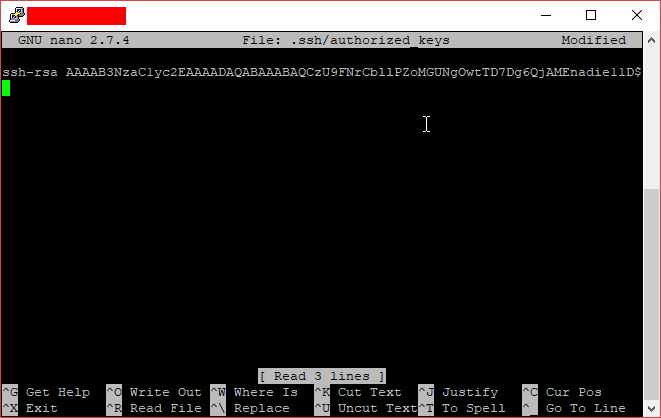
Just save the file, and from now on, you should be able to log int in the server with the session you configured in Step 1 without being asked for a password.
Bonus Step 3a: Configure Firefox to use the SSH tunnel in a separate profile
Manually changing your browser’s configuration to use the SSH tunnel every time you need to connect to your remote network is a pain. In that case, it is very easy to just create a specific profile in your preferred browser that is directly configured to use the tunnel.
In Firefox, it is as easy as running the command below (just press the Windows+R keys to get the Run command dialog):
firefox --no-remote -CreateProfile Proxy
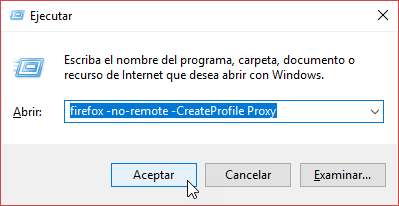
Once the profile has been created, you can just create, for example, a shortcut in your Desktop that opens that profile of Firefox by running the command:
firefox --no-remote -P Proxy
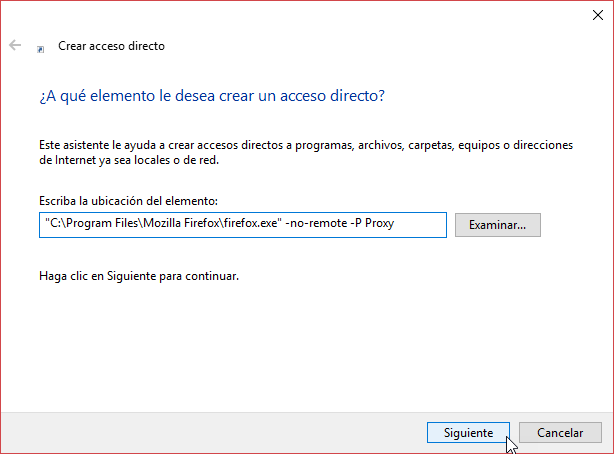
Once you have your profile properly configured in Firefox, just open it by opening the windows shortcut you have just created. Go to the Network Preferences, and set the SOCKS Proxy to localhost, and the Port to the one we configured in Step 1 (e.g., 8080). If your remote network also has some hosts that only resolve privately, you may want to enable the Proxy DNS when using SOCKS v5 option at the bottom.
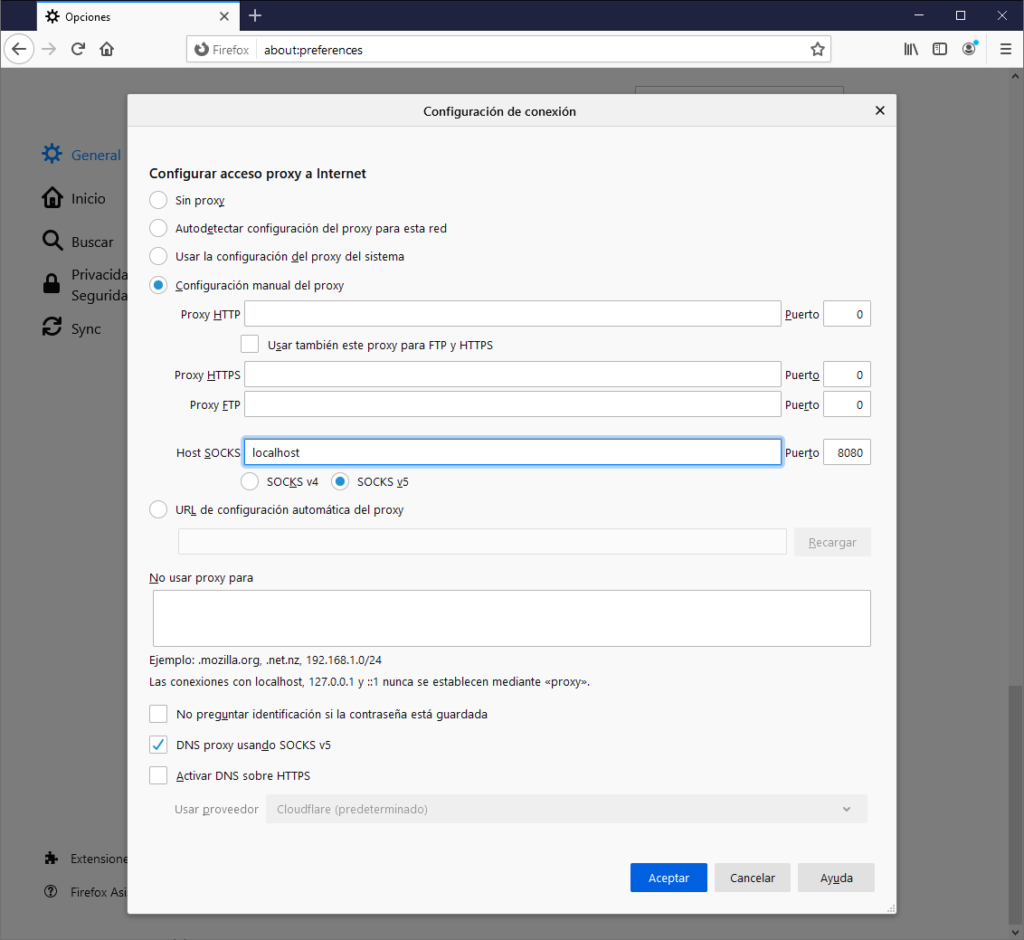
Now, you can just accept the new configuration, and you can close the preferences. If you browse the Internet using this profile, it will act as if you were browsing directly from your remote server. TA-DA!
REMEMBER: you always must open the SSH session we saved in Step 1 first in order to be able to use the SOCKS proxy we have just configured.
Bonus Step 3b: Configure Chrome to use the SSH tunnel in a separate profile
Although Google Chrome also allows using different profiles, for its network configuration it relies on the Internet configuration of the system. Nevertheless, it is possible to set a differen SOCKS proxy at startup via a command-line argument. Thus, to have a separate instance of Google Chrome capable of using our SSH tunnel without interfering with other applications or configuration, we only need to provide the --user-data-dir argument and the --proxy-server argument. E.g.:
"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --user-data-dir="%USERPROFILE%\proxy-profile" --proxy-server="socks5://localhost:8080"
In this case, we can also create a Windows Shortcut on our Desktop to directly run a Google Chrome profile that uses our SSH Tunnel (but in this case, using something similar to the above command):
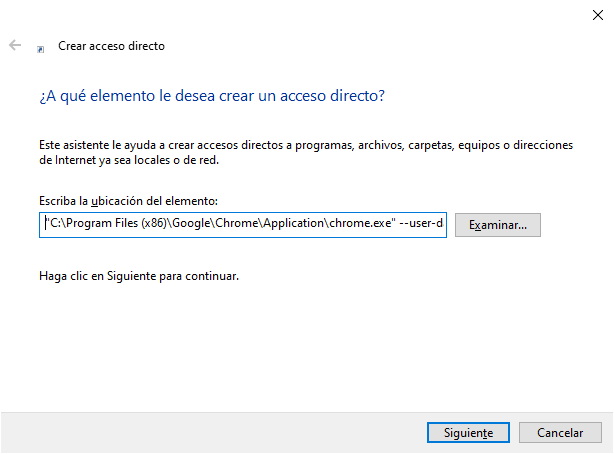
Now, just open the new Windows shortcut to Google Chrome, and enjoy your web surfing!
Again, remember that you always must open the SSH session we saved in Step 1 first in order to be able to use the SOCKS proxy we have just configured.
That’s all! enjoy!